계속 이어서 Emotet 악성코드를 분석해보겠습니다.
샘플 해시(SHA256)는 ed22dd68fd9923411084acc6dc9a2db1673a2aab14842a78329b4f5bb8453215입니다.
[Hash Resolving]
● 리졸빙 정보 수집
지난번 포스팅에서 데이터를 복호화했더니 DLL/API 이름들을 많이 볼 수 있었습니다. 샘플 DLL은 동적으로 DLL/API 이름들을 리졸빙하는 것 같습니다. 호출되는 함수들을 따라가 상황을 파악하고 같이 리졸빙을 수행하여 분석해보겠습니다..
DllRegisterServer부터 시작해보겠습니다. 첫 번째로 호출되는 서브루틴 sub_5DF1FD0으로 이동해보겠습니다.

53번째 줄의 sub_5DFEBA2 서브루틴으로 들어가보겠습니다.

특별한 것은 없었으니 6번째 줄의 sub_5DFEAA3으로 들어가보겠습니다.

sub_5DFEAA3 서브루틴에는 두 개의 호출(sub_5DE645E, sub_5DF1B22)과 수상한 16진수 숫자들이 있습니다.
그중 5번째 줄의 sub_5DE645E 서브루틴을 분석해보겠습니다.

- cdecl 호출 규약이 쓰이고 있습니다.
- 5번째 줄의 sub_5DFBFF0은 여러 개의 인수를 가지고 있습니다. 그중 마지막 인수는 해시값으로 보이는데, 이는 보통 난독화 기법이 적용된 악성코드 샘플을 분석할 때 많이 보이는 패턴입니다.
- 또한 같은 줄에서 값 또는 문자열을 로컬 변수 v1로 반환하는 것은 해시 리졸빙과 관련된 무언가가 존재한다는 지표입니다.
- 6번째 줄에서 v1이 함수 이름으로 사용되고 여러 개의 인수를 가지고 있습니다. v1은 API 이름으로 보입니다.
- 전체적인 그림으로 보니 sub_5DE645E가 래퍼(wrapper) 함수인 것 같습니다.
- 어셈블리 코드를 통해 v1 호출에 인수가 없다는 것을 확인하였기 때문에 해당 인수들이 모두 가짜 인수로 생각됩니다.

sub_5DFBFF0 서브루틴의 교차 참조를 확인해보니 109번 호출되고 있습니다.

매우 많은 횟수이므로 꽤나 의미있는 서브루틴일 것 같으니 sub_5DFBFF0 서브루틴을 자세히 분석해보면 좋을 것 같습니다.
● API 리졸빙 루틴 : sub_5DFBFF0 (mw_api_resolving)

해당 서브루틴에서 다음과 같은 사실을 알 수 있습니다.
- API 이름을 저장하는데 사용되는 것으로 보이는 dword 배열 (line 6, 9, 11)
- 스택(ecx)에서 가져온 v4 인자를 통해 sub_5E01AE9를 호출
- sub_5DFB558 호출 시의 인자 중 v5는 sub_BA1AE9에서 반환된 값이고, a4는 API 해시인 것으로 추정되는 16진수 형태의 값
내부에서 호출되는 두 개의 함수(sub_5E01AE9, sub_5DFB558)에 대해서도 분석해보겠습니다.
1) sub_5E01AE9 (mw_dll_hashing)

해당 서브루틴에서 DLL 해싱 리졸빙을 담당하고 있습니다. 올바른 DLL 이름을 찾아 해당 주소를 반환해줍니다.
6번째 줄의 sub_5DFAA52 서브루틴은 내부 NtCurrentPeb 함수를 통해 PEB(Process Environment Block)를 가져옵니다.
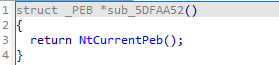
또한 같은 줄에서 Ldr 필드를 가리키고 있는데 이는 PEB_LDR_DATA 구조체를 가리키는 포인터입니다. PEB_LDR_DATA 구조체는 프로세스에 로드된 DLL 모듈을 나타냅니다.
또한 InLoadOrderModuleList는 _LIST_ENTRY 구조체를 가리키는데, 이는 더블 링크드 링스트(double linked list)를 나타냅니다.
코드에서 sub_5DF40AF를 호출하여 관련 해시를 계산한 후, 키 0x23FECA30으로 XOR 연산을 수행하고 계산된 해시와 결과를 비교합니다. 결과가 일치하면 해당 DLL의 기본 주소를 반환합니다.
위에서 얻은 정보를 기반으로 구조체를 추가하고, 변수와 서브루틴명을 변경해주겠습니다.

그리고 mw_dll_hashing_algo (sub_5DF40AF) 서브루틴 내부도 변수명을 예쁘게 변경해주겠습니다.
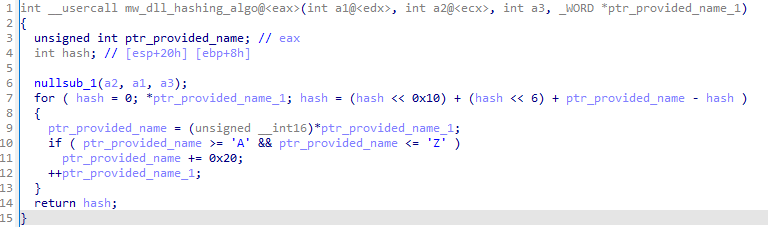
mw_dll_hashing_algo 서브루틴에 대해 알게된 점은 다음과 같습니다.
- DLL 이름에 대한 포인터를 받습니다.
- 7번째 줄에서 주어진 이름의 각 문자를 파싱하고 세 가지 연산을 합산하여 해시(hash)를 계산합니다.
- 10-11번째 줄에서 DLL 이름의 문자가 대문자인지 확인하여 대문자면 소문자로 변경합니다.
- 마지막에는 계산된 해시를 반환합니다.
sub_5DFBFF0 서브루틴 내부 두 번째 호출 함수인 sub_5DFB558 서브루틴으로 이동해보겠습니다.
2) sub_5DFB558 (mw_api_hash_resolving)

해당 서브루틴에서 주의 깊게 볼 부분은 23번째 줄입니다.
- mw_dll_hashing (sub_5E01AE9) 서브루틴과 유사한 해시 관련 연산이 있습니다. sub_5DEB099 호출 및 연산을 통한 (해시)값을 a2와 비교합니다. 여기서 이 서브루틴의 a2는 sub_5DFBFF0 서브루틴의 4번째 인자인 0x76FC34E6입니다(Figure 20).
- 연산에 사용되는 XOR 키는 0x32C9DB43으로 저번과 다릅니다.
- 실제 해싱 작업을 처리하는 서브루틴은 연산하는 부분인 sub_5DEB099일 가능성이 높습니다.
그럼 대강 파악이 됐으니 코드를 예쁘게 만들어주면 보기 좋을 것 같습니다.
먼저 표준 구조체들(_IMAGE_DOS_HEADER, _IMAGE_NT_HEADERS, _IMAGE_EXPORT_DIRECTORY)을 추가해주겠습니다.

추가한 세 개의 구조체에 의해 _IMAGE_FILE_HEADER, _IMAGE_OPTIONAL_HEADERS32, _IMAGE_DATA_DIRECTORY 구조체들은 자동으로 로드됩니다. IDA는 구조체를 로드할 때 그와 관련된 다른 구조체들을 함께 로드해주는데, 이 구조체들 모두 Windows PE 파일 포맷에서 서로 연결/연관되어 있기 때문입니다.
추가한 구조체를 바탕으로 타입도 변경해주고, 변수/서브루틴명도 바꿔주겠습니다.

내부 호출되는 함수 sub_5DEB099, sub_5DFB384 이름도 각각 mw_api_resolving_algo, mw_w_api_hash_resolving으로 바꿔주었습니다.
mw_api_resolving_algo (sub_5DEB099) 서브루틴 내부도 아래 그림처럼 변경해주었습니다.

● API 리졸빙
이 정보들을 가지고 HashDB 플러그인을 사용하여 API 이름을 리졸빙해보겠습니다.
먼저 방금 찾았던 XOR 키를 세팅하고 emotet을 선택하겠습니다. 이 DLL 샘플이 emotet이라는 것을 알고 있으니깐요ㅎ

그리고 리졸빙하려는 해시값을 찾아서 sub_5DE645E 서브루틴으로 돌아가보겠습니다(DllRegisterServer → sub_5DF1FD0 → sub_5DFEBA2 → sub_5DFEAA3 → sub_5DE645E).
해당 해시값을 오른쪽 클릭하여 HashDB Hunting Algorithm를 선택해 emotet으로 세팅한 후, 다시 해시값을 오른쪽 클릭하여 HashDB Lookup을 선택하면 다음과 같은 창이 출력됩니다. module은 kernel32를 선택해줍니다.

그리고 Eums 탭을 확인해보면 잘 추가된 hashdb_strings_emotet을 볼 수 있습니다.
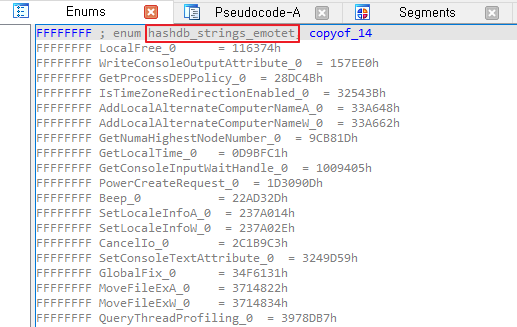
마지막으로 해시값의 타입을 바꿔주면 되겠습니다. sub_5DFBFF0 서브루틴의 마지막 인자였던 해시값의 타입을 생성한 hashdb_strings_emotet으로 변경해줍니다.

이렇게 알게된 정보를 기반으로 sub_5DE645E (mw_GetProcessHeap) 서브루틴 코드를 좀 더 예쁘게 변경해주겠습니다.

mw_GetProcessHeap (sub_5DE645E) 서브루틴은 GetProcessHeap API를 리졸빙하기 위한 proxy 함수라고 할 수 있습니다.
- Wrapper/Stub/Proxy 함수 특징
- wrapper 함수
- 원본 함수를 감싸는 함수
- 주로 원본 함수의 호출을 캡슐화하여 호출 전후에 추가적인 작업을 수행하거나 함수 호출을 더 쉽게 사용할 수 있도록 합니다.
- stub 함수
- 함수 호출의 자리를 대체하는 자리 표시자 역할의 함수
- 실제로 아무 작업도 하지 않거나 단순히 호출되는 다른 함수의 주소를 동적으로 해결하는데 사용됩니다.
- 주로 동적 링크에서 함수 주소를 해결하기 전에 일시적으로 사용됩니다.
- proxy 함수
- 함수 호출을 대리하거나 중간에서 수정하여 추가 로직을 수행하는 함수
- 원본 함수의 호출을 동적으로 조정하거나 변경하는 방식으로 호출 전후에 추가적인 작업을 수행합니다.
- 예를 들어 원본 함수가 호출되기 전에 어떤 검사를 하거나 다른 방식으로 호출을 변경하는데 사용합니다.
- wrapper 함수
API 리졸빙을 수행하는 서브루틴이 mw_api_resolving이라는 것을 알았으니까 다른 해시들도 리졸빙해주면 좋을 것 같습니다. mw_api_resolving 서브루틴의 교차 참조를 확인해보겠습니다.

위에서도 봤긴 했지만 109개로 너무 많네여....;; API 리졸빙을 모두 완료하고 코드도 예쁘게 변경해두면 분석에 도움이 많이 되겠죠 ㅎ 시간이 오래 걸릴 것 같으니 저는 패스하고 넘어가도록 하겠습니당 ^^
[C2 IP 주소 복호화]
DLL 샘플의 섹션이 3개밖에 없다는 것을 확인했었는데요.

지난번에 .text 섹션을 분석했었으니 이번에는 .data 섹션에 대해 살펴보려고 합니다.

데이터 블롭이 두 번 연속으로 0(\x00)으로 끝나는 것은 주목할만한 점이니 기억해두면 좋습니다.
우선 .data 섹션 시작 부분에 있는 데이터 dword_5E04000의 교차 참조(DATA XREF)를 따라가보겠습니다.

따라가보면 sub_5E0225A 서브루틴의 코드가 나옵니다.

해당 데이터를 인자로 호출되는 sub_5DFACFF 서브루틴에 들어가보겠습니다.

해당 서브루틴 내부에 XOR, 비트 시프트 연산이 존재하는 것을 보니 문자열을 디코딩하기 위한 루틴이라는 것을 파악할 수 있습니다. 지난 포스팅에 .text 섹션 문자열을 복호화하는 루틴(Emotet 분석(2) 포스팅 - sub_5DE4BB4 서브루틴)과 거의 동일한 내용의 코드입니다.
다른 점이라면, sub_5DFACFF 서브루틴은 .data 섹션을 복호화하고 있고, .data 섹션에 저장된 데이터는 평범한 문자열 형태가 아니라는 점입니다. 바로 전의 sub_5E0225A 서브루틴에 들어가보겠습니다.
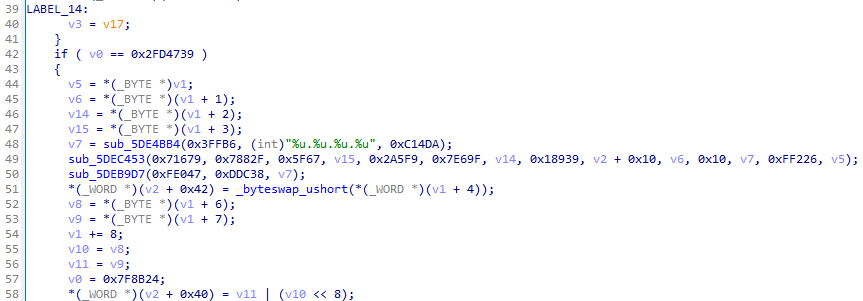
48번째 줄의 문자열 "%u.%u.%u.%u"은 딱 봐도 IP 주소 형식입니다. 이를 통해 .data 섹션의 0x05E04000부터 0x05E04208까지(Figure 23)는 암호화된 IP 주소들이라는 것을 알 수 있습니다.
복호화 루틴과 C2 IP 주소 데이터들을 얻었으니 IDA Python 스크립트를 통해 복호화해보도록 하겠습니다. (Alexandre Borges의 "Malware Analysis Series(MAS) – Article 3"를 참고하였습니다.)
import binascii
import pefile
import struct
import ipaddress
def decrypter(data_key, data_string, stringlength):
decoded = []
for i in range(0, stringlength):
decoded.append((data_string[i]) ^ (data_key[i % len(data_key)]))
return decoded
def extract_data(filename):
pe = pefile.PE(filename)
imagebase = pe.OPTIONAL_HEADER.ImageBase
for section in pe.sections:
if '.data' in section.Name.decode(encoding='utf-8').rstrip('x00'):
return (section.get_data(section.VirtualAddress, section.SizeOfRawData), (section.VirtualAddress + imagebase))
def calc_offsets(x_seg_start, x_start):
data_offset = hex(int(x_start, 16) - int(x_seg_start, 16))
return data_offset
def data_decrytper():
filename = r"C:\Users\asamin\Desktop\new_rundll32_05DE0000.bin"
data_extracted, virtualaddress = extract_data(filename)
encrypted_string_addr = hex(virtualaddress)
encr_data_rel = calc_offsets(encrypted_string_addr, encrypted_string_addr)
d1_off = 0x0
if (b'\x00\x00' in data_extracted[int(encr_data_rel, 16):]):
d1_off = (data_extracted[int(encr_data_rel, 16):]).index(b'\x00\x00')
bytes_extracted = (data_extracted[int(encr_data_rel, 16):int(encr_data_rel, 16) + d1_off])
offset = 0
xorkey = bytes_extracted[offset:(offset+4)]
xorkey_unpacked = struct.unpack('<I', xorkey)[0]
xored_length = bytes_extracted[(offset+4):(offset+4+4)]
xored_length_unpacked = struct.unpack('<I', xored_length)[0]
string_length = xorkey_unpacked ^ xored_length_unpacked
encrypted_string = bytes_extracted[8:8+string_length]
decoded_bytes = bytes(decrypter(xorkey, encrypted_string, string_length))
print('\nC2 IP ADDRESS LIST: ')
print(30 * '-')
k=0
i=0
while (k < len(decoded_bytes)):
ip_item = decoded_bytes[k:k+4]
ip_port = decoded_bytes[k+4:k+6]
print("IP[%d]: %s" % (i, ipaddress.IPv4Address(ip_item)), end=':')
print(int(binascii.hexlify(ip_port), 16))
k = k+8
i = i+1
def main():
data_decrytper()
return
if __name__ == '__main__':
main()
스크립트 실행 결과는 다음과 같습니다.

C2 IP 주소들이 잘 복호화된 걸 확인했습니다. Emotet 악성코드 분석은 여기서 마치도록 하겠습니다.
Ref. "Malware Analysis Series(MAS) – Article 3", Alexandre Borges
'Malware > malware analysis' 카테고리의 다른 글
| [Agent Tesla 분석 (2)] .NET 모듈 추출 및 분석 (0) | 2025.04.03 |
|---|---|
| [Agent Tesla 분석 (1)] .NET 분석, 난독화 해제하기(Deobfucator) (0) | 2025.03.14 |
| [Emotet 분석 (2)] 난독화된 바이너리의 특징과 .text 섹션 데이터 복호화 (0) | 2025.02.26 |
| [Emotet 분석 (1)] 파일 정보 수집 및 언패킹(Unpacking) (0) | 2025.02.21 |
| [Qakbot 분석 (5)] C2 통신 과정과 탐지 회피 및 지속성 확보 (1) | 2025.02.14 |