Qakbot 악성코드 분석 마지막 포스팅입니다.
이번 포스팅에서는 악성코드가 C2 통신하는 과정과 탐지 회피 및 지속성을 확보하는 부분을 분석해보겠습니다.
샘플 해시(SHA256)는 73e4969db4253f9aeb2cbc7462376fb7e26cc4bb5bd23b82e2af0eaaf5ae66a8입니다.
[공개키 복호]
분석 중 악성코드가 Crypto API를 호출하는 부분을 발견했습니다.
해당 서브루틴인 sub_100084AF에 들어가보겠습니다.

sub_100084AF 서브루틴 내부에서 암호 관련 API들을 호출하고 있습니다.
- CryptDecodeObjectEx
- 주어진 인코딩된 데이터를 지정된 구조체 형식으로 디코딩하는데 사용
- 주어진 인코딩된 데이터를 지정된 구조체 형식으로 디코딩하는데 사용
- CryptDecodeObjectEx 함수 구조
BOOL CryptDecodeObjectEx(
DWORD dwCertEncodingType, // 인코딩 타입 지정
LPCSTR lpszStructType, // 디코딩할 데이터의 구조체 형식 지정
const BYTE *pbEncoded, // (디코딩할) 인코딩된 데이터에 대한 포인터
DWORD dwEncodedSize, // 인코딩된 데이터의 크기
DWORD dwFlags, // 디코딩 작업 관련 작업 (ex. 메모리 자동 할당 여부, 유효성 검사 여부 등)
PCRYPT_DECODE_PARA pDecodePara, // 디코딩 작업에 대한 추가 정보
void *pvStructInfo, // 디코딩 정보를 저장할 구조체의 포인터
DWORD *pdwStructInfo // 반환될 구조체의 크기(변수)의 포인터
);
- CryptAcquireContext
- 암호화 서비스를 제공하는 프로바이더(CSP)를 획득하는데 사용
- 암호화 서비스를 제공하는 프로바이더(CSP)를 획득하는데 사용
- CryptAcquireContext 함수 구조
BOOL CryptAcquireContext(
HCRYPTPROV *phProv, // 프로바이더 핸들
LPCSTR pszContainer, // 컨테이너 이름 (NULL이면 기본 컨테이너 사용)
LPCSTR pszProvider, // 프로바이더 이름 (NULL이면 기본 프로바이더 사용)
DWORD dwProvType, // 프로바이더 유형
DWORD dwFlags // 플래그
);
- CryptImportPublicKeyInfo
- 공개 키 정보를 가져오는데(import) 사용
- 주로 X.509 인증서에서 공개 키를 추출하여 이를 암호화 작업에 사용
- CryptImportPublicKeyInfo 함수 구조
BOOL CryptImportPublicKeyInfo(
DWORD dwCertEncodingType, // 인코딩 타입
PCERT_PUBLIC_KEY_INFO pki, // 공개 키 정보 구조체
HCRYPTKEY *phKey // 반환될 공개 키 핸들
);
- CryptCreateHash
- 해시 객체를 생성하는데 사용
- 해시 객체를 생성하는데 사용
- CryptCreateHash 함수 구조
BOOL CryptCreateHash(
HCRYPTPROV *phProv, // 프로바이더 핸들
ALG_ID Algid, // 해시 알고리즘의 식별자
HCRYPTKEY hKey, // (선택 사항) 암호화 키 (일부 알고리즘에만 필요)
DWORD dwFlags, // 플래그 (예: CryptCreateHash 동작 제어)
HCRYPTHASH *phHash // 해시 객체 핸들 (출력 파라미터)
);
- CryptHashData
- 해시 객체에 데이터를 입력하여 해시 값을 계산하는데 사용
- 해시 객체에 데이터를 입력하여 해시 값을 계산하는데 사용
- CryptHashData 함수 구조
BOOL CryptHashData(
HCRYPTHASH hHash, // 해시 객체 핸들
const BYTE *pbData, // 해싱할 데이터
DWORD dwDataLen, // 데이터 길이
DWORD dwFlags // 플래그
);
- CryptVerifySignatureA
- 디지털 서명 검증을 수행하는데 사용
- 디지털 서명 검증을 수행하는데 사용
- CryptVerifySignatureA 함수 구조
BOOL CryptVerifySignatureA(
PCCERT_CONTEXT pCertContext, // 서명자 인증서의 컨텍스트
const BYTE *pbSignature, // 디지털 서명
DWORD dwSigLen, // 서명의 길이
const BYTE *pbData, // 서명 검증 대상 데이터
DWORD dwDataLen, // 검증 대상 데이터의 길이
LPCSTR szProvider // (선택 사항) 프로바이더 이름
);
sub_100084AF 서브루틴은 Crypto API를 이용하여 C2 통신과 관련된 공개 키를 처리하고 있습니다.
그리고 36번째 줄에서는 암호화된 문자열들을 XOR 연산합니다. XOR 연산되는 암호화된 데이터 mw_encrypted_string_1는 .data 섹션에 저장되어 있고, 키 mw_encrypted_string_2는 .rdata 섹션에 저장되어 있습니다.
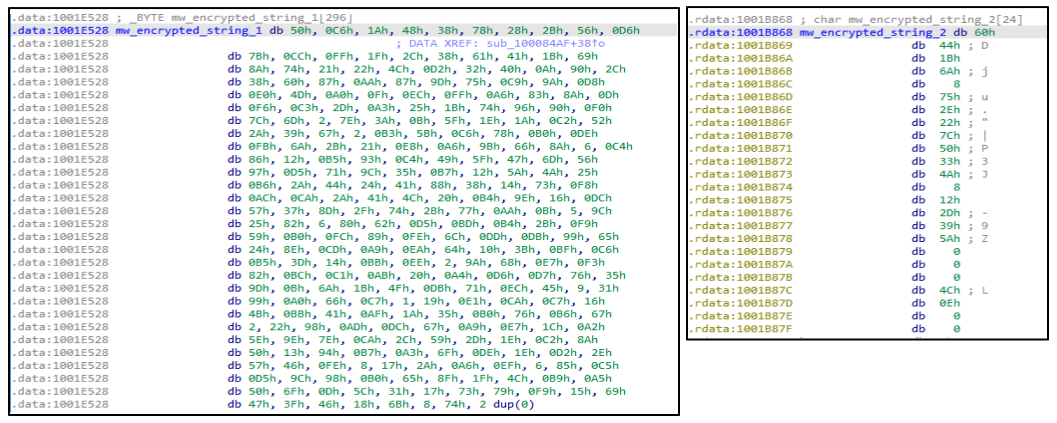
이 암호화된 데이터를 Python 스크립트를 이용하여 복호화해보겠습니다. (Alexandre Borges의 "Malware Analysis Series(MAS) – Article 2" 참조)
import pefile
import binascii
from Crypto.IO import PEM
data_seg_start = ''
rdata_seg_start = ''
# Decrypter routine used to decode the stored data.
def simple_decrypter(data_string, data_key):
decoded = ''
for i in range(0, len(data_string)):
decoded += chr((data_string[i]) ^ (data_key[i % len(data_key)]))
return (binascii.b2a_hex(decoded.encode('latin-1')))
# Routine responsible for extracting encoded bytes from .data section.
def extract_data(filename):
pe = pefile.PE(filename)
for section in pe.sections:
if '.data' in section.Name.decode(encoding='utf-8').rstrip('x00'):
return (section.get_data(section.VirtualAddress, section.SizeOfRawData))
# Routine responsible for extracting encoded bytes from .rdata section
def extract_rdata(filename):
pe2 = pefile.PE(filename)
for section2 in pe2.sections:
if 'rdata' in section2.Name.decode(encoding='utf-8').rstrip('x00'):
return (section2.get_data((section2.VirtualAddress + 0x168), section2.SizeOfRawData))
# This routine calculates the offset from start of the section until the address of the data.
def calc_offsets(x_seg_start, x_start):
data_offset = hex(int(x_start, 16) - int(x_seg_start, 16))
return data_offset
def main():
data_2 = b''
rdata_2 = b''
# Defines start of each section (.data and .rdata section) and encrypted data (data and key).
data_seg_start = '0x1001D000'
rdata_seg_start = '0x10018168'
data_start = '0x1001E528'
rdata_start = '0x1001B868'
# Calculates offset of data and key related to the start of each respective section.
data_rel = calc_offsets(data_seg_start, data_start)
rdata_rel = calc_offsets(rdata_seg_start, rdata_start)
# Defines a varialbe to hold the sample's path
filename = r"C:\Users\user\Desktop\mas2_sample_unpack\rundll32_047A0000_from_VirtualProtect.bin"
# Call extract routine to fetch all necessary bytes from .data and .rdata section.
data_1 = extract_data(filename)
rdata_1 = extract_rdata(filename)
# Looking for the end of data and key bytes.
d_off = 0x0
rd_off = 0x0
if (b'\x00\x00' in data_1[int(data_rel, 16):]):
d_off = (data_1[int(data_rel, 16):]).index(b'\x00\x00')
if (b'\x00\x00' in rdata_1[int(rdata_rel, 16):]):
rd_off = (rdata_1[int(rdata_rel, 16):]).index(b'\x00\x00')
# Collects encrypted data and key.
data_2 = data_1[int(data_rel, 16):int(data_rel, 16) + d_off]
rdata_2 = rdata_1[int(rdata_rel, 16):int(rdata_rel, 16) + d_off]
# Calls function responsible for decoding the encrypted data.
decoded_data = simple_decrypter(data_2, rdata_2)
# Format the extracted data as a public key in PEM Format.
marker = "RSA PUBLIC KEY"
pem_key = PEM.encode(decoded_data, marker, passphrase=None, randfunc=None)
print(pem_key)
if __name__ == '__main__':
main()
RSA 공개 키가 잘 복호화되었습니다.

[C2 통신 준비]
또 다른 서브루틴 sub_1000D9B1을 살펴보겠습니다.

해당 서브루틴 내부에서 mw_w_decode_string_table_1 서브루틴을 통해 복호화하는 문자열이 있습니다. ‘SELECT * FROM Win32_OperatingSystem’과 ‘ROOT\CIMv2’ 같이 WMI와 관련된 문자열입니다.
- WMI (Windows Management Instrumentation)
- Microsoft Windows 운영체제에서 제공하는 관리 및 모니터링 시스템
- 시스템 관리 및 정보 수집, 모니터링, 제어 등을 위한 프레임워크
- 시스템 하드웨어, 소프트웨어, 네트워크, 프로세스 및 다른 시스템 자원에 대한 정보를 제공하며, 시스템 관리자나 개발자가 원격지에서 시스템을 모니터링하고 제어할 수 있도록 지원
다른 정보를 얻기 위해 12번째 줄의 mw_COM_IWbemLocator (sub_1000D6D0) 서브루틴을 분석해보겠습니다.

12번째 줄에 rclsid와 riid를 발견했습니다.

- RCLSID(Reference to Class Identifier): CLSID를 참조하는 포인터
- CLSID(Class Identifier): COM 객체의 클래스를 식별하는 GUID(Globally Unique Identifier)
- CLSID(Class Identifier): COM 객체의 클래스를 식별하는 GUID(Globally Unique Identifier)
- RIID(Reference to Interface Identifier): IID를 참조하는 포인터
- IID(Interface Identifier ID): COM 객체의 인터페이스를 식별하는 GUID
발견한 ID 정보는 클래스 ID: 4590F811-1D3A-11D0-891F-00AA004B2E24, 인터페이스 ID: DC12A687-737F-11CF-884D-00AA004B2E24입니다.
클래스 ID는 Microsoft Management Console (MMC) ActiveX Control를 나타내는 것을 알 수 있습니다.
- Microsoft Management Console (MMC) ActiveX Control
- Microsoft Management Console (MMC): Windows에서 시스템 관리 및 관리 도구를 제공하는 프레임워크
- ActiveX Control: 웹 브라우저나 응용 프로그램에서 다양한 동적 기능을 제공하는 소프트웨어 컴포넌트
- MMC 기반의 관리 도구와 관련된 웹 관리 기능을 제공
- 시스템 관리 또는 원격 관리와 관련된 작업에서 사용
또한 인터페이스 ID는 IWbemLocator 인터페이스를 참조한다는 것을 알 수 있습니다.
- IWbemLocator
- WMI에서 사용되는 COM 인터페이스로 시스템 관리, 상태 모니터링 및 자동화를 위한 API
- 클라이언트 애플리케이션이 WMI 네임스페이스에 연결하고 WMI 서비스에 접근할 수 있도록 지원
이 정보를 토대로 ppv와 ptr_buffer 타입을 바꿔 코드를 이해하기 쉽게 만들었습니다.

14번째 줄에 ConnectServer 메서드를 발견할 수 있습니다.
- ConnectServer
- WMI 네임스페이스에 연결하고, 연결된 IWbemServices 인터페이스를 반환
- 해당 메서드를 통해 WMI 서비스 연결을 설정하여 WMI 작업을 수행
- ConnectServer 함수 구조
HRESULT ConnectServer(
const BSTR strNetworkResource, // 네트워크 리소스
const BSTR strUser, // 사용자 이름
const BSTR strPassword, // 비밀번호
const BSTR strLocale, // 지역 설정
long lSecurityFlags, // 보안 플래그
const BSTR strAuthority, // 인증 정보
IWbemContext* pCtx, // WMI 컨텍스트
IWbemServices** ppServices // 연결된 WMI 서비스 객체 반환
);
IWbemLocator 인터페이스는 IWbemLocator::ConnectServer 메서드를 통해 WMI 네임스페이스에 연결을 생성하고, 반환되는 IWbemServices를 통해 WMI 쿼리나 작업을 실행하는데 사용합니다.
처음에 본 'ROOT\CIMv2’ 문자열은 ConnectServer의 첫 번째 파라미터인 strNetworkResource를 통해 전달되는데, 해당 파라미터는 WMI 네임스페이스의 객체 경로를 포함하는 네트워크 리소스를 의미합니다.
mw_COM_IWbemLocator의 래퍼 함수인 sub_1000DCE9 (mw_w_COM_IWbemLocator) 서브루틴을 들어가보겠습니다.
IWbemLocator인 것을 파악했으니 변수 타입과 이름을 그에 맞게 바꿔줘서 가독성을 높여보겠습니다.

49번째 줄의 mw_COM_IWbemLocator 함수 결과 타입은 IWbemServices *이므로 result 변수 타입을 IWbemServices *으로 변경해주었습니다.
또한 80번째 줄의 v7 변수 타입을 IWbemServices **로 변경해주면 아래 그림의 82번째 줄에서 IWbemServices::ExecQuery가 호출되는 것을 확인할 수 있습니다.
- ExecQuery
- WMI에 대해 질의하여 그 결과로 반환된 데이터를 받아오는 메서드
- WMI에 대해 질의하여 그 결과로 반환된 데이터를 받아오는 메서드
- ExecQuery 함수 구조
HRESULT ExecQuery(
const BSTR strQueryLanguage, // 쿼리 언어를 지정하는 문자열
const BSTR strQuery, // 실행할 쿼리 문자열
long lFlags, // 쿼리 실행에 대한 플래그
IWbemContext *pCtx, // IWbemContext 객체에 대한 포인터
IWbemObjectSet **ppResults // 쿼리 결과를 담을 IWbemObjectSet에 대한 포인터
);
76번째 줄에서 문자열 복호화 루틴을 통해 'WQL' 문자열이 복호화되었는데 이는 WMI에서 사용하는 쿼리 언어로, ExecQuery의 파라미터로 지정되는 것을 확인할 수 있습니다.

82번째 줄에서 보이듯이 ExecQuery의 반환값 ppEum은 IEumWbemClassObject **타입입니다. ppEum은 이미 참조가 있기 때문에 ppEum와 함께 84번째 줄 v9 변수의 타입을 IEumWbemClassObject *으로 변경해주었습니다.
그러면 91번째 줄에 IEumWbemClassObject::Next 메소드가 잘 보입니다.
- Next
- IWbemObjectSet의 결과 객체 집합에서 다음 객체로 이동하거나 다음 객체를 가져오는 데 사용
- IWbemObjectSet의 결과 객체 집합에서 다음 객체로 이동하거나 다음 객체를 가져오는 데 사용
- Next 함수 구조
HRESULT Next(
long lTimeout, // 대기 시간 (밀리초 단위, 0이면 즉시 반환)
long lNumObjectsRequested, // 요청할 객체의 수
IWbemClassObject **ppObjects, // 반환될 객체들의 배열
long *plNumObjectsReturned // 실제 반환된 객체 수
);
Next도 비슷하게 세 번째 인수인 v38의 타입이 IWbemClassObject **이지만 참조가 존재하므로, IWbemClassObject *으로 변경해주겠습니다.
그러면 99번째 줄에 IWbemClassObject::GetNames와 106번째 줄에 Release 메서드가 보입니다.
- GetNames
- WMI 클래스의 속성 이름을 가져오는데 사용
- GetNames 메서드는 각 속성에 대해 IWbemClassObject::Get 메서드를 사용하여 접근할 수 있도록 함
- GetNames 메서드를 통해 속성 이름을 가져오고, Get 메서드를 통해 각 속성의 값을 가져옴
- GetNames 메서드를 통해 속성 이름을 가져오고, Get 메서드를 통해 각 속성의 값을 가져옴
- GetNames 함수 구조
HRESULT GetNames(
BSTR strQualifierType, // 자격 유형 (보통 NULL을 사용)
long lFlags, // 플래그 (기본값 0)
IWbemContext *pCtx, // 쿼리 컨텍스트 (기본값 NULL)
SAFEARRAY **pNames // 속성 이름이 저장될 SAFEARRAY 배열
);
- Release
- COM 객체의 참조 카운트를 관리하는 메서드
- COM 인터페이스에서 공통적으로 사용됨
[기타 행위 분석]
○ 레지스트리 설정

sub_1000A23A (mw_RC4_Reg) 서브루틴 내부를 보니 레지스트리 관련 API들이 보이고, 이전 포스팅에서 분석했던 SHA1 및 RC4 관련 서브루틴들이 보입니다. 이를 통해 레지스트리 항목을 암복호화하기 위해 똑같은 암복호화 방식(key → SHA1 → RC4)을 사용하고 있다는 것을 알 수 있습니다.
○ Defender 탐지 회피
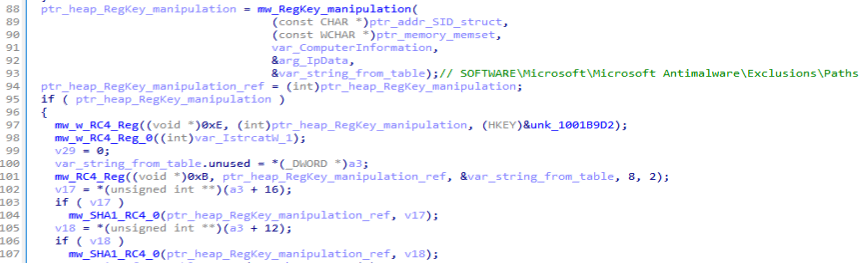
초기 키는 sub_10004C5A 서브루틴에서 피해자의 컴퓨터 이름, 계정, 볼륨 정보를 기반으로 SHA1 해시 함수를 통해 생성됩니다.
또한 문자열 "SOFTWARE\Microsoft\Microsoft Antimalware\Exclusions\Paths"을 복호화하는 것으로 보아 악성코드 자신을 Windows Defender에서 예외로 설정하는 것을 알 수 있습니다.
○ 언어(국가) 정보 수집

sub_10002E98 (mw_GetKeyBoardLayoutList) 서브루틴에는 GetKeyBoardLayoutList API를 통해 키보드 레이아웃을 확인하는 코드가 있습니다.
- GetKeyboardLayoutList
- 현재 사용 가능한 모든 키보드 레이아웃을 배열 형태로 반환
키보드 레이아웃을 확인하여 24-28번째 줄의 연산을 통해 피해 PC의 언어 설정을 알아내는 것을 알 수 있습니다.
악성코드 개발자는 v6 배열에 국가 목록을 미리 지정해두고, 해당 국가의 언어를 사용하는 사용자라면 악성 행위를 진행하도록 설정하였습니다. 주로 구소련 국가들과 관련이 있는 것 같습니다.
| LCID | 국가 | 언어 |
| 0x4019 | 러시아 (Russia) | 러시아어 |
| 0x4023 | 벨라루스 (Belarus) | 벨라루스어 |
| 0x403F | 우크라이나 (Ukraine) | 우크라이나어 |
| 0x402C | 카자흐스탄 (Kazakhstan) | 카자흐어 |
| 0x402B | 아제르바이잔 (Azerbaijan) | 아제르바이잔어 |
| 0x4037 | 타지키스탄 (Tajikistan) | 타지크어 |
| 0x4043 | 우즈베키스탄 (Uzbekistan) | 우즈벡어 |
| 0x4028 | 몽골 (Mongolia) | 몽골어 |
| 0x4042 | 영국 (United Kingdom) | 영어 |
| 0x4022 | 그루지야 (Georgia) | 그루지야어 |
| 0x401A | 아르메니아 (Armenia) | 아르메니아어 |
| 0x4040 | 조지아 (Georgia) | 조지아어 |
○ Avast 탐지 회피 및 지속성 확보

sub_10004FB9 서브루틴에서는 문자열 복호 루틴을 통해 aswhooka.dll, aswhokkx.dll 문자열을 복호화한 후, 해당 DLL들에 대해 핸들을 얻고 있습니다. 해당 DLL들은 보안 소프트웨어 Avast와 관련이 있기 때문에 핸들을 얻어 보안 프로그램의 탐지 회피, 비활성화 및 제어 등의 행위를 할 것으로 추측됩니다.

또한 작업 스케줄 설정과 관련된 "C:\Windows\system32\schtasks.exe” /Create /RU "NT AUTHORITY\SYSTEM" /tn <random name> /tr <program path> /SC ONCE /Z /ST <(start)hour:min> /ET <(terminate)hour:min>, regsvr32.exe -s 문자열을 복호화하고, 152번째 줄에서 mw_CreateProcess (sub_1000AAC1)를 호출하여 스케줄 명령을 프로세스로 실행합니다. 이렇게 지속성을 확보하는 부분도 확인하였습니다.
아래는 mw_CreateProcess 서브루틴입니다.

- CreateProcessW
- 새로운 프로세스를 생성
- 유니코드 문자열을 사용하는 버전
- CreateProcess: ANSI 문자열을 사용하는 버전
- CreateProcess: ANSI 문자열을 사용하는 버전
- CreateProcessW 함수 구조
BOOL CreateProcessW(
LPCWSTR lpApplicationName, // 실행할 애플리케이션의 경로 (유니코드 문자열)
LPWSTR lpCommandLine, // 실행할 명령 줄 (유니코드 문자열)
LPSECURITY_ATTRIBUTES lpProcessAttributes, // 프로세스 보안 속성 (NULL이면 기본값)
LPSECURITY_ATTRIBUTES lpThreadAttributes, // 스레드 보안 속성 (NULL이면 기본값)
BOOL bInheritHandles, // 부모 프로세스의 핸들 상속 여부 (TRUE/FALSE)
DWORD dwCreationFlags, // 프로세스 생성 플래그 (예: CREATE_NEW_CONSOLE)
LPVOID lpEnvironment, // 새 프로세스의 환경 변수 (NULL이면 부모 환경 사용)
LPCWSTR lpCurrentDirectory, // 새 프로세스의 현재 디렉터리 (NULL이면 부모 디렉터리 사용)
LPSTARTUPINFO lpStartupInfo, // 새 프로세스의 시작 정보 (창 모양 등 설정)
LPPROCESS_INFORMATION lpProcessInformation // 새 프로세스의 정보 (핸들, 프로세스 ID 등 반환)
);
Ref. "Malware Analysis Series(MAS) – Article 2", Alexandre Borges
'Malware > malware analysis' 카테고리의 다른 글
| [Emotet 분석 (2)] 난독화된 바이너리의 특징과 .text 섹션 데이터 복호화 (0) | 2025.02.26 |
|---|---|
| [Emotet 분석 (1)] 파일 정보 수집 및 언패킹(Unpacking) (0) | 2025.02.21 |
| [Qakbot 분석 (4)] 리소스 복호화 루틴 파악 및 정보 추출 (0) | 2025.02.12 |
| [Qakbot 분석 (3)] 중첩 구조체/열거형(enum) 생성 및 mersenne twister (0) | 2025.02.10 |
| [Qakbot 분석 (2)] PE 포맷 조작 및 API 리졸빙 (0) | 2025.02.04 |