지난 포스팅에 이어 Qakbot 악성코드를 분석해보겠습니다.
이번 포스팅에서는 악성코드의 리소스 복호화 루틴을 파악하고 스크립트를 작성하여 해당 리소스에서 어떤 정보를 추출할 수 있는지 확인해보겠습니다.
샘플 해시(SHA256)는 73e4969db4253f9aeb2cbc7462376fb7e26cc4bb5bd23b82e2af0eaaf5ae66a8입니다.
계속 분석하기 위해 sub_1000FB74 서브루틴을 살펴보겠습니다.
문자열 테이블 디코더(mw_decode_string_table_2)를 호출하는 것을 발견하였습니다. 지난번 작성한 IDA Python 스크립트를 이용하여 문자열을 복호화하여 주석으로 추가해주겠습니다.
(스크립트 내용은 '바이너리에서 암호화된 문자열 추출(복호화)하기'에 자세히 설명되어 있습니다.)


sub_1000FABA (mw_manipulate_persistence) 서브루틴 또한 내부에 복호화된 문자열이 주석으로 추가되었습니다.

문자열 및 호출되는 API를 통해 레지스트리와 작업 예약을 통해 지속성을 설정함을 알 수 있습니다.
Capa 분석을 통해 HTTP 상태 코드를 확인하는 서브루틴이 존재한다는 것을 알고 있었습니다.

해당 서브루틴 sub_1000E815 (mw_HTTP_stuff)를 살펴보면

WinINet API들을 호출하고 있습니다.
그렇다면 악성코드가 WinINet API를 이용하여 특정 IP 주소인 C2와 통신하고 있다는 것입니다.
더 자세히 분석해보기 위해서 sub_1000E815 (mw_HTTP_stuff) 서브루틴의 교차 참조를 따라가보겠습니다.
(mw_HTTP_stuff → sub_1000EBE2 → sub_1000EBE1 → sub_1000729B → sub_1000719F)
sub_1000EBE2 서브루틴은 HttpQueryInfoA, InternetReadFile 등을 통해 C2 통신을 수행하고

sub_1000EBE1은 sleepEx 함수를 통해 sub_1000EBE2의 호출 간격을 관리합니다.

sub_1000729B 서브루틴에서 호출하는 sub_1000719F를 자세히 살펴보겠습니다.

sub_1000719F (mw_SHA_RC4)

지난 번 봤던 mersenne twister 함수도 있고, SHA1 관련 함수인 mw_w_SHA1 (sub_10007118)도 보입니다.
mw_w_SHA1로 들어가보겠습니다.

16번째 줄 mw_SHA1 (sub_1000F681) 서브루틴 내부 초반 코드 부분에서 암호화 상수 데이터를 볼 수 있습니다.
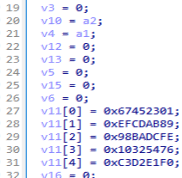
mw_w_SHA1 서브루틴의 반환값인 mw_RC4_init (sub_1000F353) 서브루틴에서는 약간 수정된 KSA(Key-scheduling algorithm) 알고리즘을 볼 수 있습니다.

S-Box(S_array) 초기화 및 섞기(재배열) 과정이 잘 나타나있습니다.
- KSA (Key-scheduling algorithm)
- RC4 같은 스트림 암호에서 사용되는 키 스케줄링 알고리즘
다시 mw_SHA_RC4로 돌아와서 18번째 줄의 mw_RC4_ PRGA 서브루틴을 보면,

mw_w_SHA1에서 반환된 키 스트림 key_stream을 다시 mw_RC4_ PRGA (sub_1000F3C5)함수 호출에 파라미터로 쓰이고 있습니다.

이를 통해 mw_RC4_PRGA가 RC4의 PRGA 루틴인 것을 알 수 있습니다.
- PRGA (Pseudorandom Generation Algorithm)
- 의사난수 생성 알고리즘
- RC4 같은 스트림 암호를 생성할 때 필요한 의사난수를 생성
RC4 알고리즘을 사용해서 악성코드가 무슨 일을 하고 있는지 궁금하니 교차 참조를 확인해보겠습니다.

여러 번 호출되고 있고 그중 sub_10008F17 서브루틴으로 이동해보겠습니다.

sub_10008F17 (mw_w_RC4)의 교차 참조를 확인하면 sub_100089C6 서브루틴이 있습니다.

sub_100089C6 (mw_ww_RC4) 내부에는 mw_SHA와 mw_w_RC4 호출이 있었습니다.
그리고 mw_ww_RC4의 교차 참조를 확인했을 때 발견한 sub_10008AC1 서브루틴에 들어가서,
sub_10008AC1 서브루틴에 대한 교차 참조 중 sub_10002783를 선택해보겠습니다.

sub_10002783 서브루틴을 자세히 보겠습니다.

sub_10002783 서브루틴 내부에는 resource를 가져오는 sub_1000A6CA (mw_get_resources) 서브루틴과
이미 분석했던 문자열 복호화 루틴 mw_w_decode_string_table_0 (sub_10001080),
또다른 resource 관련 sub_10008AC1 (mw_w_resource_crypto) 서브루틴을 호출하고 있습니다.
특히 sub_10008AC1 (mw_w_resource_crypto) 서브루틴은 mw_ww_RC4의 교차 참조를 확인했을 때 발견한, 처음에 왔던 그 서브루틴입니다.
sub_10002783 서브루틴 내부 변수/서브루틴명을 수정하여 주겠습니다.

mw_get_resources (sub_1000A6CA) 서브루틴으로 들어가보겠습니다.

해당 서브루틴은 바이너리의 .rsrc 섹션에서 리소스 데이터를 찾아 로드합니다.
- FindResourceA
- 리소스 파일에서 특정 리소스를 찾는 기능을 제공
- FindResourceA 함수 구조
- 리소스 파일에서 특정 리소스를 찾는 기능을 제공
HRSRC FindResourceA(
HMODULE hModule, // 리소스가 포함된 모듈의 핸들
LPCSTR lpName, // 찾고자 하는 리소스의 이름
LPCSTR lpType // 리소스의 유형 (예: RT_ICON, RT_STRING 등)
);
- SizeofResource
- 리소스 크기 반환
- 리소스 크기 반환
- LoadResource
- 리소스를 메모리에서 사용할 수 있도록 로딩
다시 mw_get_resources로 돌아가서, 교차 참조를 확인해보겠습니다.

그중 sub_1000173B (mw_resource_decryptor)를 살펴보겠습니다.

58번째 줄에서 리소스 식별자 3719가 제공됩니다.
59번째 줄 mw_get_resources를 통해 리소스 데이터를 가져옵니다.
66번째 줄에서 특정 문자열이 복호화됩니다.
67번째 줄에서 가져온 리소스 데이터를 복호화합니다.
mw_w_resource_crypto_0과 mw_resource_decryptor 서브루틴을 통해 알 수 있는 것은,
리소스 식별자(ID) 5812, 3719를 기반으로 리소스 데이터를 가져오고, 그것을 복호화하기 위한 mw_w_resource_crypto 함수, 그리고 mw_ww_RC4 서브루틴을 호출한다는 것입니다.
또한 SHA1 및 RC4 관련 서브루틴(mw_SHA, mw_w_RC4, mw_ww_RC4 등)을 통해 알 수 있는 것은,
키가 SHA1 서브루틴에 제공되고, SHA1 서브루틴의 결과(key_stream)가 RC4 서브루틴에 제공되며(이때 SHA1는 KDF), RC4 서브루틴은 리소스 데이터를 반환한다는 것입니다.
너무 길고 많아서 까먹지 않게 정리해봤습니다. (으윽;;)
이번에는 mw_resource_decryptor의 교차 참조 중 sub_100019DE 서브루틴을 살펴보겠습니다.

sub_100019DE 서브루틴 내부에 inet_ntoa 함수를 발견했습니다.

- inet_ntoa
- IPv4 주소를 문자열 형식으로 변환
inet_ntoa 함수를 통해 IP주소를 문자열 형식(dotted-decimal)으로 변환하는 것입니다. mw_resource_decryptor가 .rsrc에서 데이터를 가져오니깐 해당 섹션에 C2 주소가 저장되어 있을 것 같습니다.
이번에는 mw_resource_decryptor의 교차 참조 중 sub_1000173B 서브루틴을 살펴보겠습니다

내부에 보니 딱 봐도 IP 주소 형식의 문자열이 있습니다: "%u.%u.%u.%u"%u"

이렇게 .rsrc 섹션에 중요한 정보들이 있으니 .rsrc 섹션 정보를 추출하고 복호화해보면 좋을 것 같습니다.
먼저 코드에서도 확인했지만 Resource Hacker 툴로 다시 한 번 보면, 두 개의 리소스 ID가 있는 것을 알 수 있습니다.

분석을 통해 알고 있는 상황은
mw_w_RC4 서브루틴이 두 번 호출되어 두 리소스 ID를 복호화하고 있고,
mw_w_RC4 호출 시(mw_w_RC4(0x14u, (int)key, key + 20, resource_size - 20, *arg_key_stream);) 세 번째 파라미터에서 20을 더하는 것을 보면 실제 데이터는 21번째 바이트부터 시작하고 있습니다.
SHA1의 해시값이 20바이트이기 때문에 이와 연관이 있을 것입니다.
이 정보들을 기반으로 Python 스크립트를 작성하여 복호화해보겠습니다. ("Alexandre Borges의 "Malware Analysis Series(MAS) – Article 2" 참조)
import binascii
import pefile
import ipaddress
from Crypto.Cipher import ARC4
from Crypto.Hash import SHA1
# Key found in the code (doubled slashs because the interpretation)
key = b'\\System32\\WindowsPowerShell\\v1.0\\powershell.exe'
# SHA hash of the key
sha1_key = SHA1.new(data=key).digest()
# This routine extracts data from .rsrc section.
def extract_resource(filename, res_identification):
extracted_data = b""
pe = pefile.PE(filename)
for resource in pe.DIRECTORY_ENTRY_RESOURCE.entries:
if hasattr(resource, 'directory'):
for res_id in resource.directory.entries:
if hasattr(res_id, 'name'):
if (str(res_id.name) == str(res_identification)):
offset = res_id.directory.entries[0].data.struct.OffsetToData
resid_size = res_id.directory.entries[0].data.struct.Size
extracted_data = pe.get_memory_mapped_image()[offset:offset+resid_size]
return extracted_data
# This routine decrypt resource data using RC4 + hashed key
def data_decryptor(key_data, data):
data_cipher = ARC4.new(key_data)
decrypted_config = data_cipher.decrypt(data)
return decrypted_config
# Main routine used to perform all necessary calls.
def main():
# Path to the malware
filename = r"C:\Users\user\Desktop\mas2_sample_unpack\rundll32_047A0000_from_VirtualProtect.bin"
# Extracts the second resource id (smaller) and decrypt it.
resource_data = extract_resource(filename, 5812)
hex_resource_data = binascii.hexlify(resource_data)
# Remember that the useful data strat at 21th byte onward.
decrypted_data = data_decryptor(sha1_key, resource_data)[20:]
# Prints SHA1 key
print('SHA1 KEY: ', end='')
print(binascii.hexlify(sha1_key))
print(60*'=')
# Prints decrypted resource : ID=5812
print('\nDECRYPTED BOTNET AND CAMPAIGN ID: ', end='')
print("\n" + 34*'-')
print(decrypted_data.decode('latin1'))
# extracts the first resource id and decrypt it.
resource_data = extract_resource(filename, 3719)
decrypted_data = data_decryptor(sha1_key, resource_data)
# Remember that the useful data start at 21th byte onward.
resource_item = decrypted_data[21:]
# Prints decrypted resource : ID=3719
# The format is: [4 bytes for IP address][2 bytes of part]
print('\nC2 IP ADDRESS LIST: ')
print(30*'-')
k = 0
i = 0
while (k < len(resource_item)):
ip_item = resource_item[k:k+4]
ip_port = resource_item[k+4:k+6]
print("IP[%d]: %s" % (i, ipaddress.IPv4Address(ip_item)), end=':')
print(int(binascii.hexlify(ip_port),16))
k = k+7
i = i+1
if __name__ == '__main__':
main()
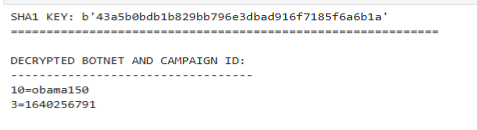
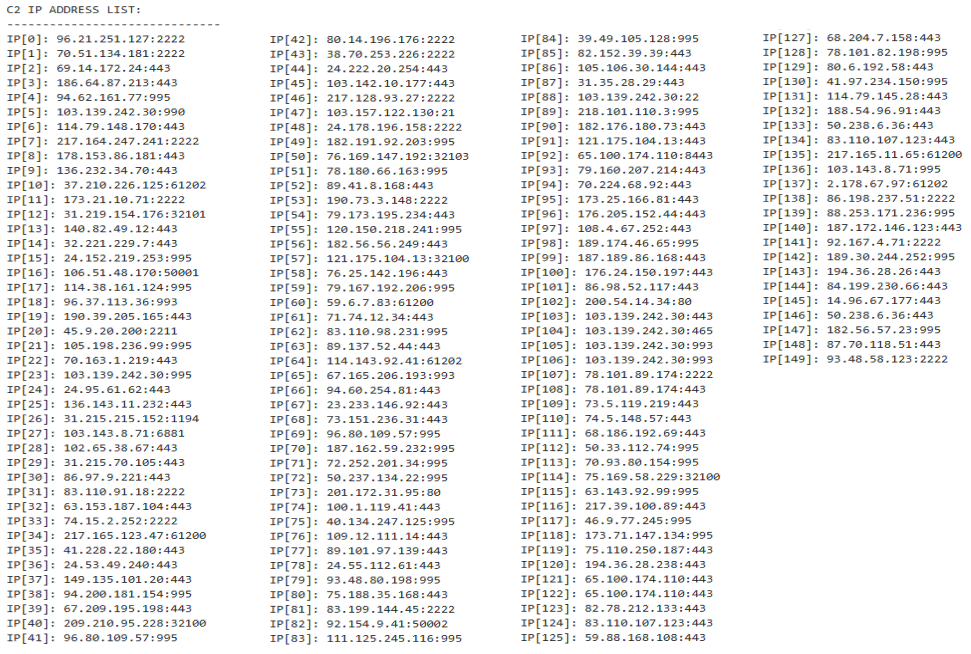
스크립트를 통해 봇넷 이름이 obama150이라는 것과 캠페인 ID가 1640256791이라는 것, 그리고 C2 IP 주소 150개를 얻었습니다.
다음 포스팅에서는 악성코드가 Crypto API를 호출하여 C2 통신하는 부분에 대해 분석해보겠습니다.
Ref. "Malware Analysis Series(MAS) – Article 2", Alexandre Borges
'Malware > malware analysis' 카테고리의 다른 글
| [Emotet 분석 (1)] 파일 정보 수집 및 언패킹(Unpacking) (0) | 2025.02.21 |
|---|---|
| [Qakbot 분석 (5)] C2 통신 과정과 탐지 회피 및 지속성 확보 (1) | 2025.02.14 |
| [Qakbot 분석 (3)] 중첩 구조체/열거형(enum) 생성 및 mersenne twister (0) | 2025.02.10 |
| [Qakbot 분석 (2)] PE 포맷 조작 및 API 리졸빙 (0) | 2025.02.04 |
| [Qakbot 분석 (1)] 언패킹(Unpacking) - 매핑과 언매핑(Mapping&Unmapping) (1) | 2025.01.17 |